Kaseya REvil Ransomware Attack
July Blog - Kaseya REvil Ransomware Attack From Our Cybersecurity Specialist Harsh Pancal
COVID19 has not only affected our lives but has also changed the way businesses operate and work. Many businesses are now moving towards cloud infrastructure and outsource their services to cloud providers. Kaseya is one of the largest Managed Service Providers (MSPs) who manages and provides various IT and Cybersecurity services around the world. One of the services is called Kaseya VSA. Kaseya VSA is a cloud-based SaaS (Software-as-a-Service) product that the company has developed to help other businesses manage, maintain and automate their IT services all in one portal.
On the 2nd of July 2021 when most of the Kaseya IT team were preparing to leave for the extended Independence Day holiday weekend in the US, they identified various services and systems that were compromised with the REvil ransomware attack. According to a Dutch cyber security organisation (DIVD), attackers were using a SQLi zero-days vulnerability (CVE-2021-30116) in Kaseya VSA servers that have been identified and already reported by the security researcher Victor Gevers weeks before the attack. This was one of the largest supply chain ransomware attacks that happened in the shortest time in history.
"Wietse Boonstra, a DIVD researcher, has previously identified a number of the zero-day vulnerabilities [CVE-2021-30116] which are currently being used in ransomware attacks. And yes, we have reported these vulnerabilities to Kaseya under responsible disclosure guidelines (aka coordinated vulnerability disclosure)." Victor Gevers, DIVD Chair |
Kaseya provides their VSA product to many businesses to use on-premises or in a cloud-based environment to manage and maintain their IT systems. Hundreds of businesses have been affected by this cyberattack including one of the largest Swedish supermarket chains Coop. Due to the attack, they had to shut more than 500 stores on Friday and Kaseya had to shut down their cloud-hosted servers for emergency maintenance, due to the REvil ransomware attack on Kaseya's VSA product. Kaseya has shared an update and claimed about 40 MSP businesses are affected who support more than 1000 small businesses however, the numbers are still expanding quickly. They've also shared their detection tool that helps to detect and identify the presence of the SQLi vulnerabilities (CVE-2021-30116).
The firm believes that the REvil is a Russian-linked ransomware gang, also known as Sodinokibi. Revil who provides Ransomware-as-a Service (RaaS) is funded by GOLD SOUTHFIELD cyber-crime group provides the backend infrastructure and operates on underground forums. REvil was first advertised on a Russian language cybercrime forum in June 2019. Each infected system has the following ransom note and demands 44,999 USD to decrypt each system.
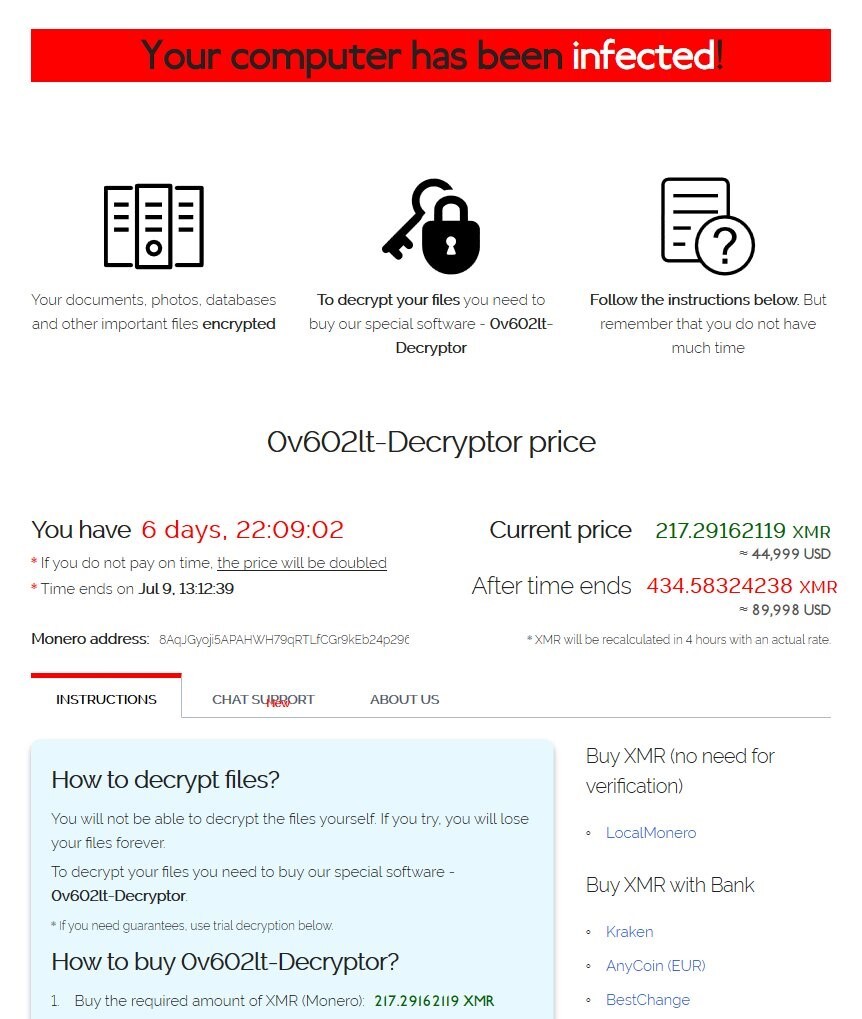
Image Source: https://www.welivesecurity.com/2021/07/03/kaseya-supply-chain-attack-what-we-know-so-far/?s=09
Huntress is a cybersecurity and incident response company currently investigating the Kaseya incident. They have published an update on the 4th July 2021 at 22:08 ET, stating that REvil has shared an update on their dark website and asking for USD 70,000,000 to decrypt all victims.

Image Source: https://twitter.com/_johnhammond/status/1411868939903246338?s=19
FBI has also published a statement on the Kaseya ransomware attack stating that "If you feel your systems have been compromised as a result of the Kaseya ransomware incident, we encourage you to employ all recommended mitigations, follow guidance from Kaseya and the Cybersecurity and Infrastructure Security Agency (CISA) to shut down your VSA servers immediately and report your compromise to the FBI at ic3.gov." asking organisations using the software to follow Kaseya's advisory guideline and report if they have been affected by this cyber-attack to help businesses to identify if they have been a victim of the vulnerabilities.
Kaseya is still investigating this incident along with the FBI to stop the spread and find an alternative solution to help recover businesses.
Related Articles
CONTACT US TODAY: